Disabling Windows Security Features
Windows includes several security features like Exploit Protection and Control Flow Guard that help protect against malware and exploits. However, these features can sometimes interfere with certain applications, requiring them to be disabled.
Disabling Exploit Protection
Method 1: Through Windows Security
-
Open Windows Security:
- Press
Windows + Ito open Settings - Navigate to
Privacy & Security>Windows Security - Click
Open Windows Security
- Press
-
Access Exploit Protection:
- Click
App & Browser control - Select
Exploit protection settings
- Click
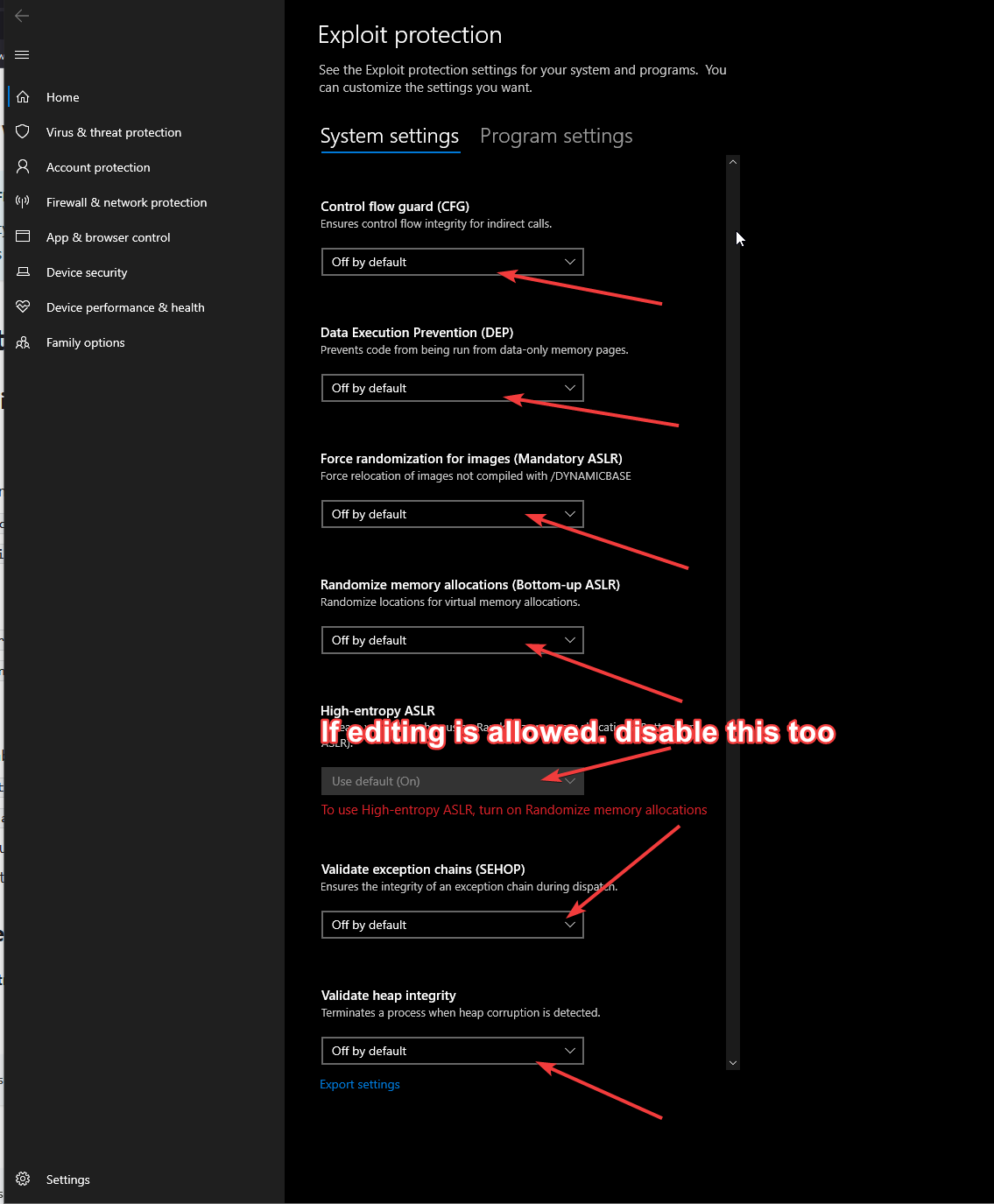
- Modify Program Settings:
- Click
Program settingstab - Click
Add program to customize - Choose
Add by program name - Enter your program's executable name
- Disable all protections for the program
- Click
Method 2: Using PowerShell (System-Wide)
-
Open PowerShell as Administrator
-
Export Current Settings:
Get-ProcessMitigation -System > settings.xml -
Disable Exploit Protection:
Set-ProcessMitigation -System -Disable CFG,DEP,AuditSEHOP,SEHOP,StrictHandle,TerminateOnError
Method 3: Registry Editor
-
Open Registry Editor:
regedit -
Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management -
Modify Values:
- Create DWORD
MoveImages=0 - Set
EnableCfg=0
- Create DWORD
Disabling Control Flow Guard (CFG)
Method 1: Visual Studio Project
If you're a developer, disable CFG in your project:
- Open project properties
- Navigate to C/C++ > Code Generation
- Set
Control Flow GuardtoNo
Method 2: System-Wide Disable
-
Registry Modification:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v EnableCfg /t REG_DWORD /d 0 /f -
Verify with PowerShell:
Get-ProcessMitigation -System | Select CFG
Additional Security Features
Data Execution Prevention (DEP)
-
Command Line Disable:
bcdedit.exe /set {current} nx AlwaysOff -
Through System Properties:
- Open System Properties
- Advanced tab > Performance > Settings
- Data Execution Prevention
- Choose "Turn on DEP for essential Windows programs only"
Address Space Layout Randomization (ASLR)
-
Registry Disable:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v MoveImages /t REG_DWORD /d 0 /f -
PowerShell Command:
Set-ProcessMitigation -System -Disable ASLR
SEHOP (Structured Exception Handler Overwrite Protection)
Set-ProcessMitigation -System -Disable SEHOP
Creating Exclusions for Specific Programs
-
Export Default Settings:
Get-ProcessMitigation -System > default_settings.xml -
Create Program-Specific Rules:
Set-ProcessMitigation -Name "program.exe" -Disable CFG,DEP,ASLR,SEHOP
PowerShell Script for Complete Disable
# Save current settings
Get-ProcessMitigation -System > "C:\security_backup.xml"
# Disable all protections
Set-ProcessMitigation -System -Disable CFG,DEP,ASLR,SEHOP,StrictHandle
Set-ProcessMitigation -System -Reset
# Disable via registry
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v EnableCfg /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v MoveImages /t REG_DWORD /d 0 /f
# Disable DEP
bcdedit.exe /set {current} nx AlwaysOff
- Create a system restore point before making changes
- Some changes require a system restart
- Windows Updates might re-enable these features
- Document all changes for future reference
Verifying Changes
Check CFG Status
Get-ProcessMitigation -System | Select CFG
Check DEP Status
bcdedit.exe /enum {current} | findstr nx
Check ASLR Status
Get-ProcessMitigation -System | Select ASLR
Restoring Security Features
-
Using Backup:
Set-ProcessMitigation -PolicyFilePath "C:\security_backup.xml" -
Reset to Windows Defaults:
Set-ProcessMitigation -System -Reset -
Enable through Registry:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v EnableCfg /t REG_DWORD /d 1 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v MoveImages /t REG_DWORD /d 1 /f
For additional support or specific program configurations, contact our support team.